Tl;dr SOPHTIX Security Team escalated to Domain Administrator in a “black box” internal penetration test using an ESC8 vulnerability in Active Directory Certificate Services (ADCS).
Enumeration
One of the most common steps in obtaining a foothold in an Active Directory environment is compromising user accounts, that allow future lateral and horizontal movement.
When Kerberos authentication is used an unauthenticated attacker can enumerate user accounts in the domain using a wordlist, since the server itself returns a “user does not exist” for a bad username: 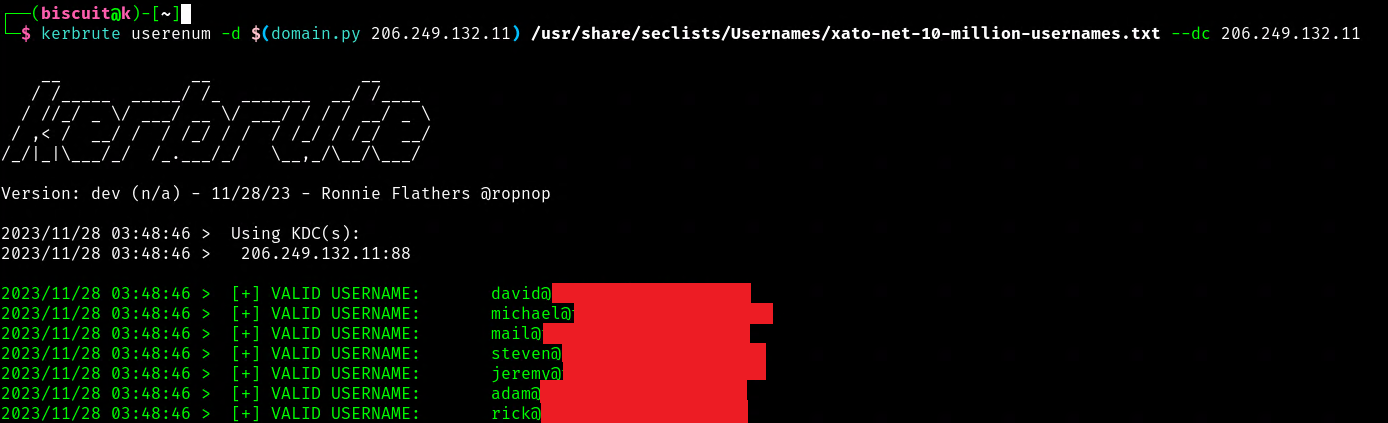
Spraying widely-used passwords in large networks often proves resourceful:

RDP login is allowed, and so we took over target\health and changed its password.
Upon further enumerating the Certificate Templates using Certipy and the newly acquired “health” credentials, an ESC8 vulnerability shows: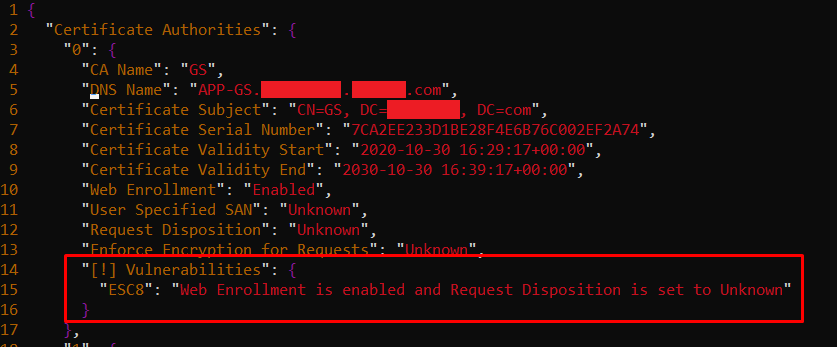
According to Crowe’s blogpost , ESC8 arises as a result of HTTP endpoints that allow for client authentication. These are vulnerable to NTLM relay attacks by design, and can be used in the context of coercion of machine accounts to authenticate to those, and ultimately exfiltrate hashes or intercept other sensitive information to move laterally and vertically.
Exploitation
In this specific engagement, the host machine was connected to an office switch physically, running a Linux guest. Using Windows’ built-in portproxy interface and the shutting down of “Server” service, the host’s SMB port (445) on the ethernet interface was proxied to the guest’s same port.

